A small, exciting, and beginner-friendly report by Guy Podjarny (Founder of Snyk) introduces you to Cloud-Native Application Security (CNAS) and Dev-First approach to help security teams achieve it.

Source: O'Reilly
Link to the book/report: https://www.oreilly.com/library/view/cloud-native-application/9781098105631/
Disclaimer: This book contains images from Snyk’s dashboard to illustrate some points for a dev-first approach (but doesn’t market about Synk). So after reading this you might be biased towards Synk products.
Summary
Businesses tend to move towards the DevOps approach (with short release cycles and more automation) and use the cloud as much as possible. This transition gives birth to Cloud-Native apps where the application and the infra are created with the cloud environment in mind (think prod/stag environments, scaling, etc).
The interesting part of this DevOps transition is that devs are now responsible for things outside their apps (like managing containers, IaC, API gateways, closing unwanted ports, etc).
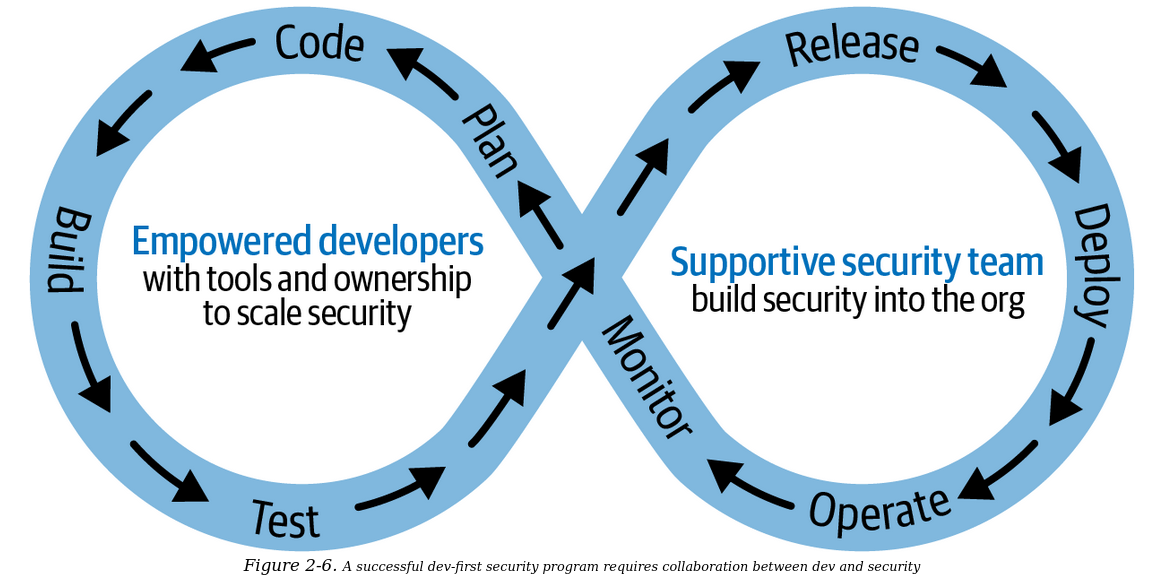
Security teams need to adapt and have a dev-first security approach that has tools/practices useful for devs (to detect & fix the security issues).
This little book has four chapters:
- Digital Transformation
- Dev-First Security
- Securing the Entire Cloud Native app
- Adapting to Dev-First CNAS
The first chapter gives a general introduction to business transformation to utilize the cloud, DevOps, and Cloud-Native apps. It talks about the changing attack surface with the introduction of cloud-native apps compared to traditional deployments.
The second chapter shows how shift-left isn’t clear in a DevOps environment and why security teams should follow a dev-first approach along with DevSecOps practices.
The third chapter introduces you to containers and Infrastructure as Code (IaC) concepts and ways to secure them in brief. The final chapter comments on rethinking security org structure, tooling, and priorities to adapt to dev-first cloud-native app security (CNAS).
Notes & Quotes
2. Dev-First Security
The reponsibility of who-owns-what changes with introduction of DevOps. Devs do more than create applications. They now build containers to run the apps and required infrastructure using IaC tools like Terraform.
“the shorter the gap between writing a bug and finding it, the cheaper it is to fix it.”
Shift-left for DevOps isn’t entirely clear because:
- DevOps is a continuous process (infinite loop), and there’s no extreme left/right. Sometimes it’s better to find the security issue after deployment than add a time-consuming security stage in CI/CD pipeline.
- Shift left doesn’t reflect the change in ownership and drive for independent teams.
DevSecOps is a very broad term, and those using it typically mean one of three things:
- Adapting security to DevOps technologies, such as containers, IaC, or the elastic compute cloud itself
- Adapting security to DevOps practices, such as continuous deployment, elastic scaling, or observability
- Adapting security to the DevOps shared ownership mindset, driving cultural change toward seeing security as everybody’s responsibility
DevSecOps is focused on ops changes and “rotates around the convergence of SecOps and DevOps practices and the post-deployment world, covering topics such as managing cloud infrastructure, runtime observability, and incident response processes”.
Dev-First security approach is a bit different than DevSecOps. The major difference is that it focuses on the folks who fix the issue rather than those who detect and manage it.
3. Securing the Entire Cloud Native app
Although developers could easily spin up infrastructure, they aren’t proficient/well equipped to manage and secure it over time.
Securing containers as apps:
- Test containers early, even before CI/CD kicks in (by using pre-build checks)
- Focus on fixing flaws, not just finding them
- Invest in base image management and relating vulns to them
- Introduce container security gates in your CI/CD to prevent bad insecure builds deployed to prod
Securing IaC as apps:
- Find issues early, before the infra exists (by analyzing source code, using tools like tfsec, Hashicorp Sentinal, etc)
- Invest in fixing IaC source code
- Automate IaC testing
New terminologies learned:
- Runtime Application Self-Protection (RASP) tools
- Cloud Security Posture Management (CSPM) tools
- Software Composition Analysis (SCA) tools
