Testing HTTP methods with Meth0dMan
Are you looking for a tool to test different HTTP verbs over URL / API endpoints ? Then the BurpSuite extension Meth0dMan is for you.
How to use ?
- Right click on the request you want to test and click on “Send to Meth0dMan”.
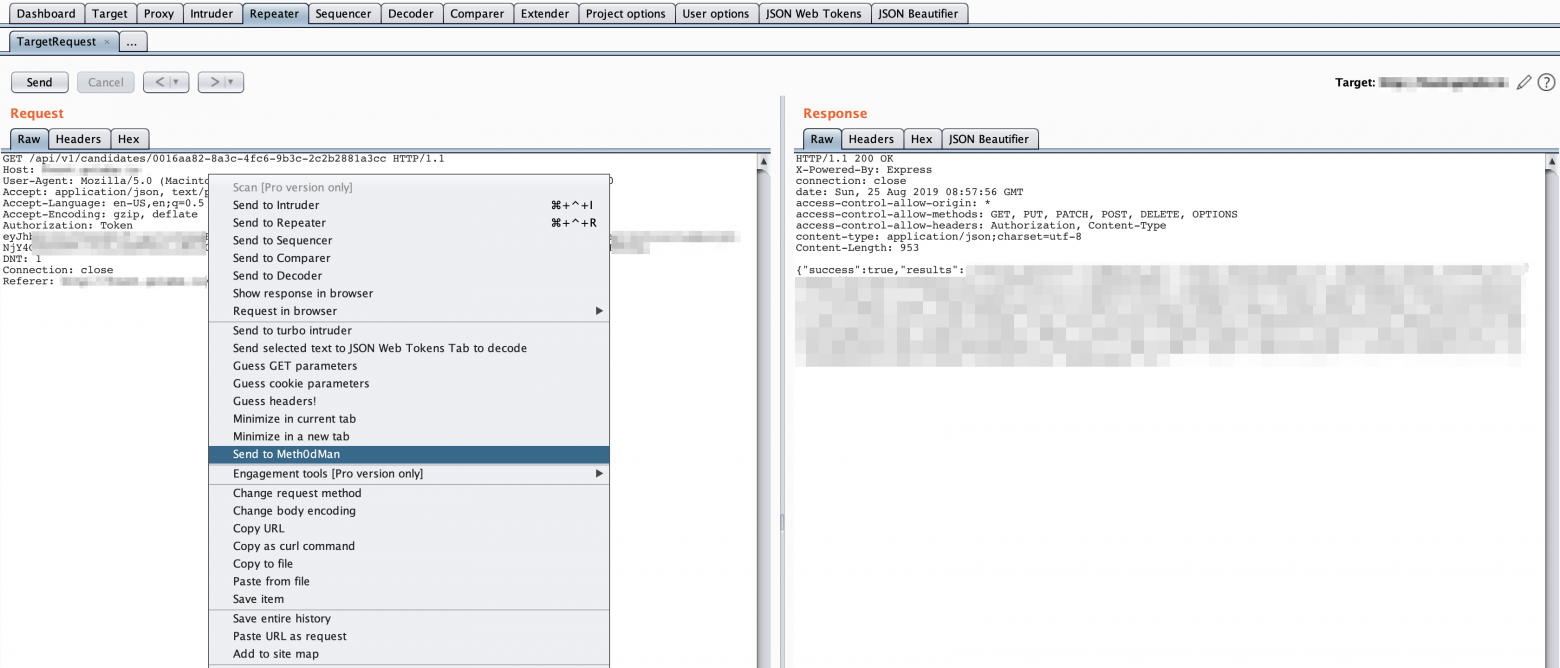
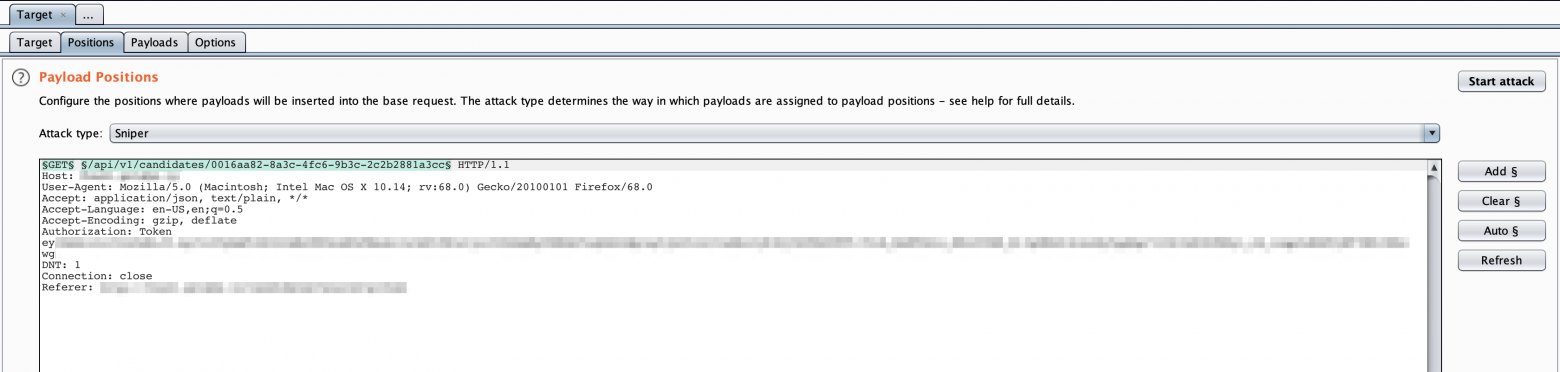
- The request is sent to Intruder. The HTTP verb and the URI endpoint is automatically highlighted.
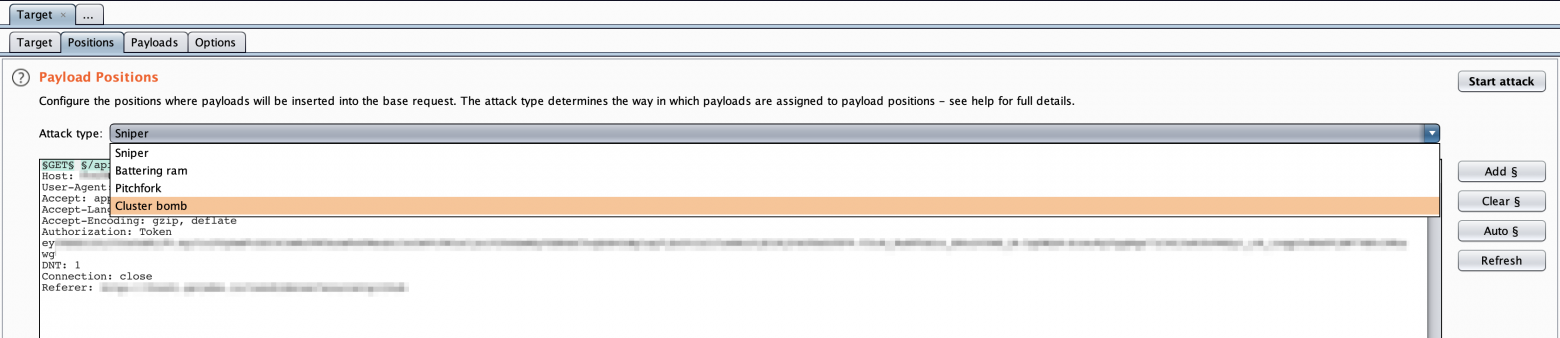
- Select the Attack Type to be “Cluster bomb”.
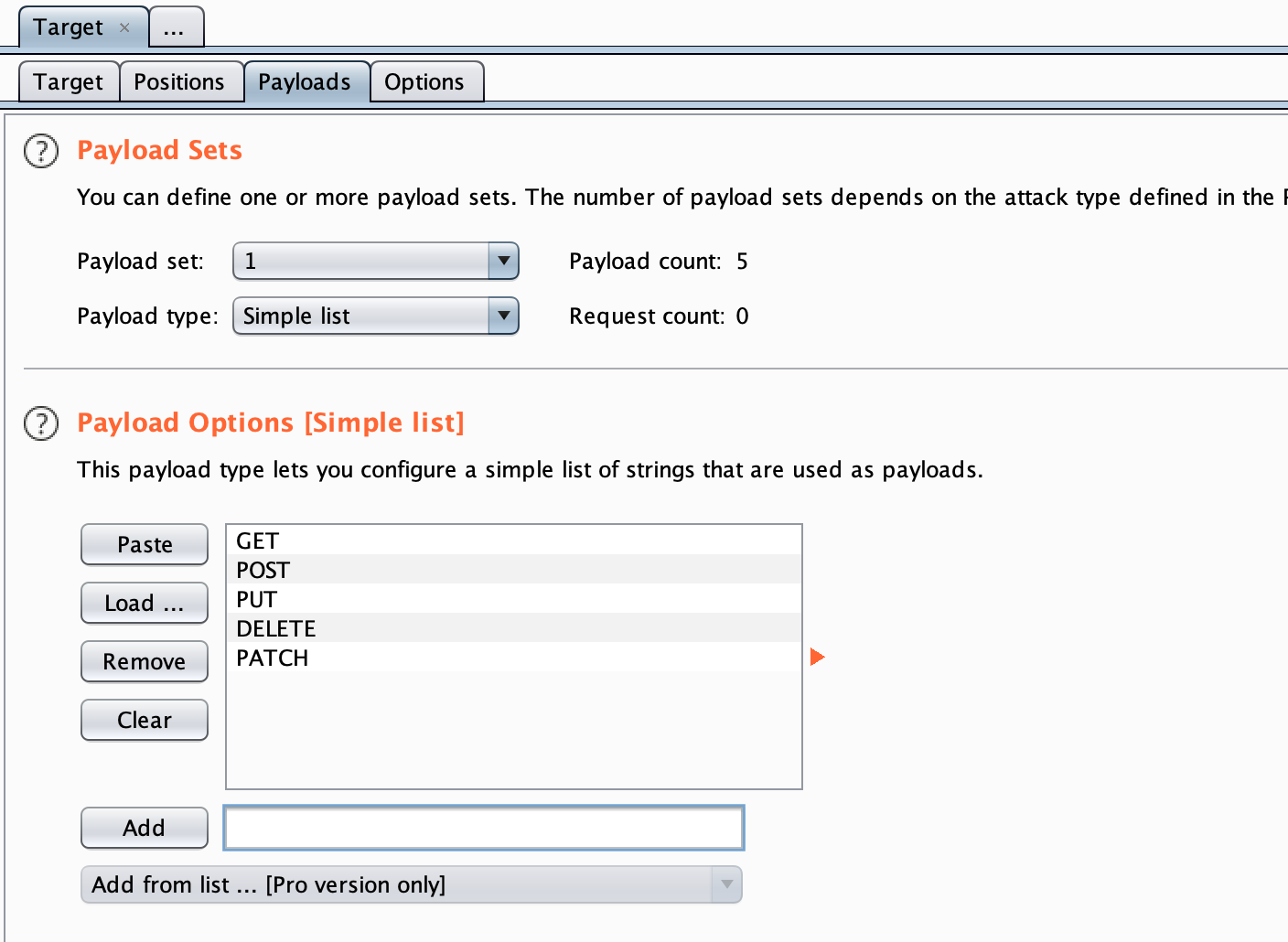
- For the first Payload Set, enter the HTTP verbs.
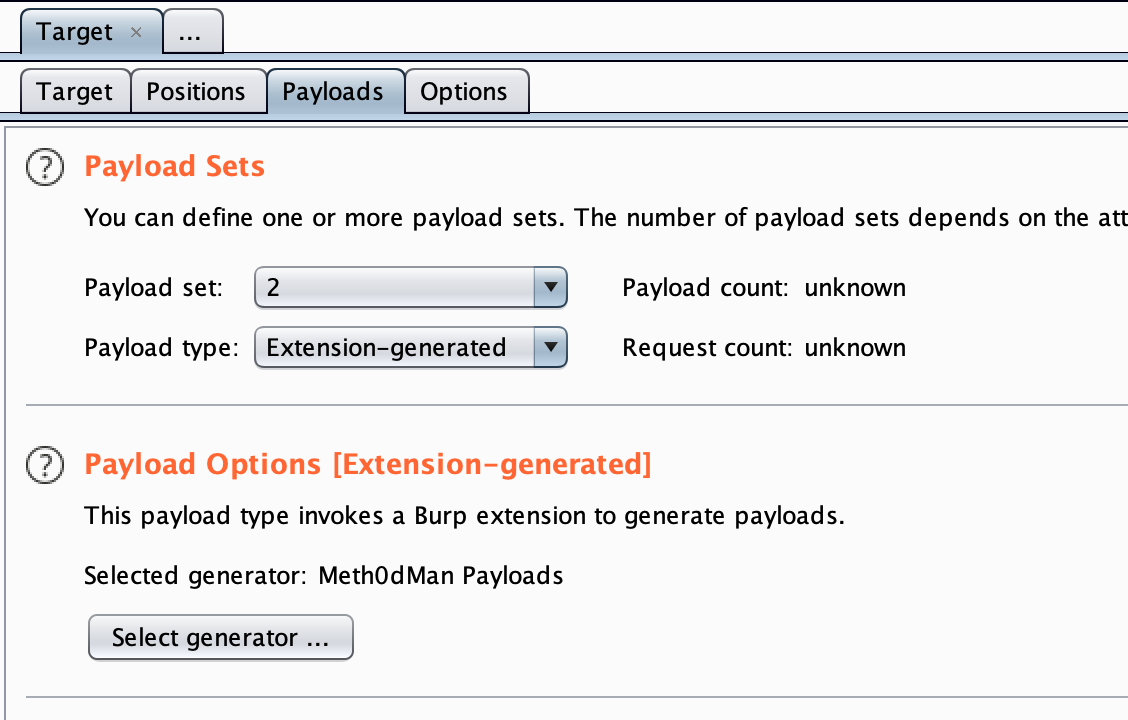
- For the second, select the Payload type to be “Extension-generated” and select the payload generator as “Meth0dMan Payloads”
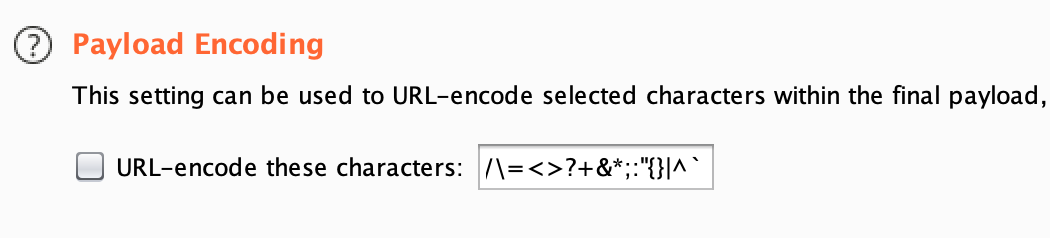
- Make sure that Payload Encoding is unticked. If not, the URI endpoints (mostly slash
/) would get encoded and will result in 400 Bad Request response from server.
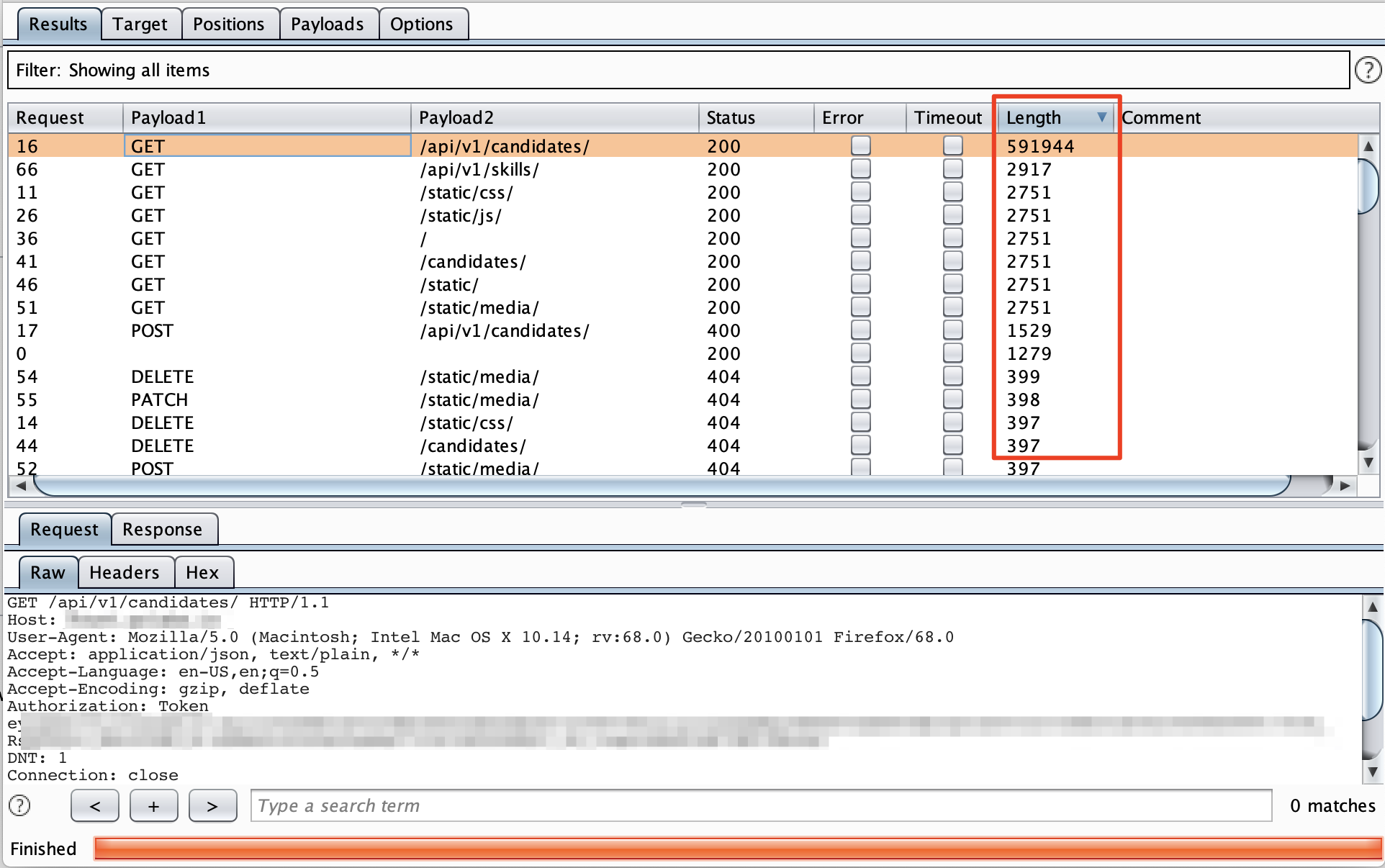
Once the attack is completed, the extension would have tested all combinations of HTTP verbs on different permutations / endpoints gathered from the response.
External Links
Source code: https://github.com/portswigger/meth0d-man
×
